Design
Overview
SnabbWall is a modular, application-level (Layer-7) firewall suite for Snabb.
As a modular system, it provides a set of components which can be reused in other Snabb designs.
As an application-level (Layer-7) firewall, it is able to:
- Inspect network traffic and detect flows of related data, and pinpoint which application has produced a certain data flow.
- Filter (drop, reject, or accept) packets using criteria specified in a set of rules, which can use the information inferred by inspecting the packets.
As a suite, it includes a complete firewall program out of the box.
Architecture
SnabbWall takes advantage of the separation in functional components, called applications in Snabb jargon. The following diagram contains a simplified view of the system:
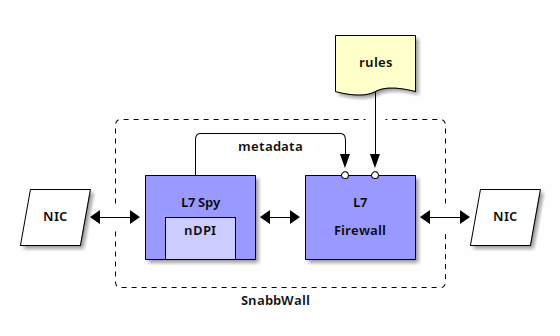
Building blocks
The main components are L7 Spy and L7 Firewall, both are Snabb applications:
- L7 Spy (or
L7spyin short) inspects ingress network traffic, identifies related packets to group them in a related data flow, and —if possible— determines which application has generated the data flow. This is done with the aid of the nDPI packet inspection library. The information gathered is attached to each packet as metadata, and the packets are passed through unmodified. - L7 Firewall (or
L7fwin short) receives a set of filtering rules, tries to match ingress packets with each rule, and performs its associated action. The rules can perform matches on the metadata generated by the L7 Spy application.
Applications
L7 Spy
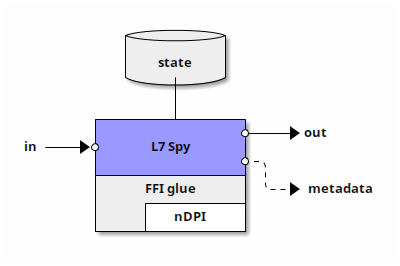
L7 Spy application
The L7 Spy (L7spy) application receives packets from another Snabb application as input, analyzes the packets it receives, and places them unchanged in the output. As a by-product of analyzing the packets, it may generate metadata indicating the kind of application and data payload that the packet contains. This metadata is de-coupled from the original packet data —which remains unchanged— and can be consumed by other Snabb applications-
Each instance of the L7spy application maintain an internal state which is updated as each packet is scanned. It contains information about previously inspected packets which is used to further improve identification of packets in the future. The state is detached from the L7fw application and two (or more) instances can share the same state:
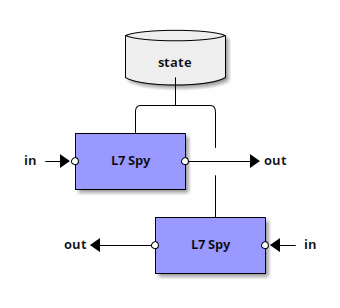
Using a shared L7 Spy state
The main use case for a the shared state is correlating traffic which belongs to the same application flowing in both “send” and “receive” directions.
L7 Firewall
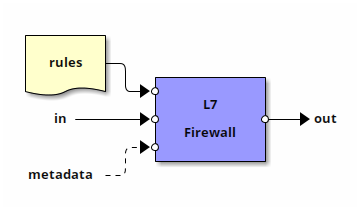
L7 Firewall application
The L7 Firewall (L7fw) application receives packets from another Snabb application as input, applies a set of packet filtering rules, and either drops, rehects, or accepts the packet.
- Dropping a packet plainly ignores it, without forwarding it to the output. The net effect is the same as if the packet were lost.
- Rejecting, similarly, does not forward it to the output, but the sender of the packet is notified about the inability of delivering the packet by transmitting the appropriate ICMP messages to the sender.
- Accepting a packet forwards it to the output, effectively letting it pass through the firewall.
Note that the application by itself is unidirectional. While this may seem counterintuitive, allows for greater flexibility:
- Bidirectional filtering —both “send” and “receive” directions— is achieved using two instances with an optionally shared set of rules.
- In many scenarios filtering is done in one direction only, and it is possible to use a single instance of the application — with reduced overhead. For example, most —if not all— of the work done by a firewall in front of a server is to only accept packets for the services provided by the server.
Programs
The SnabbWall suite ships with a ready to use program which uses the L7 Spy and L7 Firewall applications to implement a Layer-7 stateful firewall.
This application, runnable using the snabb wall command, includes support for the following features:
- Loading its configuration and filtering rule sets from from configuration files. The syntax of the configuration files is an internal DSL based on Lua. This takes advantage of the fact that the language is particularly well suited for data description.
- Support for dropping, rejecting, or accepting packets matched by the filtering rules.
- Specifying a default policy (drop, reject, or accept) for packets which are not matched by any of the configured filtering rules.
- Optional logging and accounting of matched packets.
- Operating in bypass mode: using two physical NIC endpoints at each side, the traffic received from both sides is analyzed using L7spy, rules are applied using L7fw, and packets allowed to pass through the firewall are put into the wire at the other side completely unchanged.
- Operating in hosted mode: the firewall appears to the host system as a pair of network interfaces (one for each end). In this mode the host system needs to be configured accordingly to forwarding packets into and out of the firewall.
- Operating in kitchen sink mode: the firewall passively scans all input packets and gathers information about them, without forwarding them to the output. This can be used together with the logging and accounting support to obtain per-application network statistics.
